Its equally (relatively) trivial to block that. Xephyr runs another X ... such that a window running on X0 (DISPLAY:0), can't stuff/read things into/from X1 (DISPLAY:1).
Combine that with unshare, capabilities (capsh ... such as being able to drop the capability to chroot), along with chroot ... and Barry with his EasyOS has provided great guidance as to how to create 'containers'.
I've been experimenting with using a chroot into / ... instead of a pre-created chroot folder/directory. Using / ... and everything is already set up.
First we create a Xephyr (another) X instance (DISPLAY:1)
Code: Select all
Xephyr :1 -fullscreen -dpi 133 -title chroot -br -nolisten tcp -nolisten local &
PID=$!Code: Select all
echo "#!/bin/sh" >/CHR
echo "DISPLAY=:1 export DISPLAY" >>/CHR
echo "rox -p /root/Choices/ROX-Filer/PuppyPin" >>/CHR
echo "jwm" >>/CHR
chmod +x /CHRCode: Select all
DISPLAY=:1 unshare -p -m --mount-proc=/proc -f capsh --drop=cap_sys_admin,cap_sys_boot,cap_sys_chroot,
cap_sys_ptrace,cap_sys_time,cap_sys_tty_config,cap_chown,
cap_kill,cap_dac_override,cap_dac_read_search,cap_fowner,
cap_setfcap,cap_setpcap,cap_net_admin,cap_mknod,
cap_sys_module,cap_sys_nice,cap_sys_resource --chroot=/ -- /CHR
kill $PIDThose capsh drops work relatively well, but you can use capsh --print to view what capabilities remain, or you might remove some from the above set ... according to whatever your objective. Those settings worked OK in both EasyOS 1.0.8 and FatDog 8.0 RC (i.e. when the above lines of code were dropped into a script file with #!/bin/sh at the top). Within the chroot you're still root, but a root with restricted permissions, a duff-root (which in effect is comparable to a restricted userid).
Xephyr as above is set to run fullscreen. Best perhaps to change that to --resizeable at first, until you become more familiar with how it all works (remember you can use alt-tab to flip between windows, or alt-F6 to minimise the window. Opening a terminal and running jwm -exit will close the session, or you can just switch to the main real root session and right click the tray entry and select the close option).
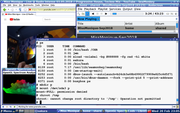
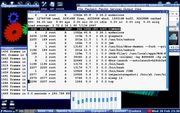
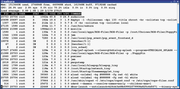
Within the above settings, the chroot can read/write files etc. as usual, but whilst its root its a disabled root. Run ps within the chroot for instance and you only see a limited set of processes. Try and chown a file and ... not permitted. Try and chroot out of the chroot and ... not permitted. Try and mount sda3 (or whatever) and not permitted, but you can see sda3 files if they were already mounted by the 'real root'. Try and use tools to spy or enter keys into real root and ... not permitted. Run a browser and that's fine, or any other program (subject to not relying upon capabilities that have been dropped).
A word of caution for running that in Fatdog. As Fatdog chroot's seamonkey to spot, then when you run defaultbrowser (assuming that is set to seamonkey) it will complain that it cannot chroot (as we've dropped the chroot capability), and fires up the browser as root (but the duff-root). Would be better perhaps to also add a --user=spot parameter, but I haven't tested/tried that.
Clickable thumbnail. I created the ps terminal first (trying a few things such as chroot, mounting sda3), then added other windows (seamonkey viewing a youtube, audacious, libreoffice spreadsheet ... all running under the duff-root (Xephyr/unshare/capsh/chroot)).